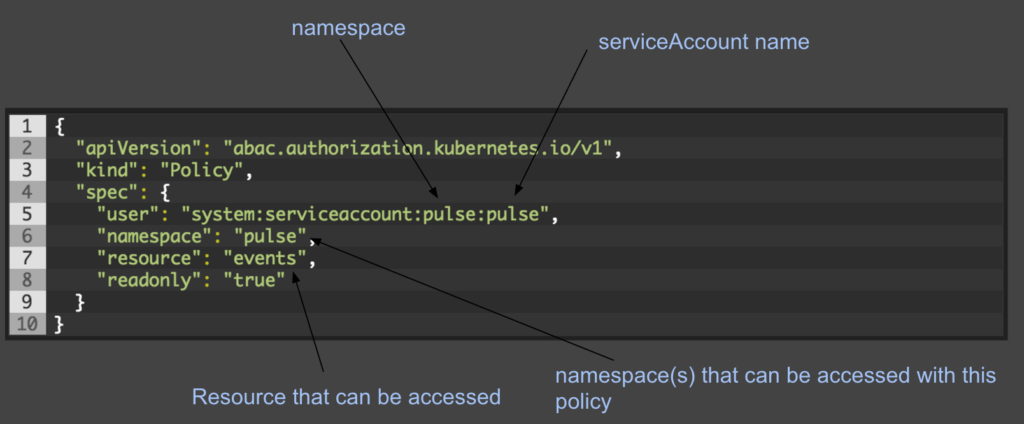
came up with it one morning around 4am while trying to get the baby to sleep.
i’m pretty proud. mostly because it works 😉
– Andy Moore
As many of you know, my team began integrating StackStorm with Kubernetes via ThirdPartyResources(TPR) which we showed off at KubeCon_London in March 2016. This was a great start to our integrations with Kubernetes and allowed us to expand our capabilities around managing datastores simply by posting a TPR to the Kubernetes API. Allowing StackStorm to build/deploy/manage our database clusters automatically.
This however only worked with ThirdPartyResources. In fact, it only worked with the ‘beta’ TPRs which were significantly revamped before making it into GA.
With that Andy Moore figured out how to automatically generate a StackStorm pack crammed full of exciting new capabilities for both StackStorm Sensors and Actions.
Link:
https://github.com/pearsontechnology/st2contrib/tree/bite-1162/packs/kubernetes
You will notice this has not been committed back upstream to StackStorm yet. Our latest version diverges significantly from the original pack we pushed and we need to work with the StackStorm team for the best approach to move forward.
@stackstorm if you want to help us out with this, we would be very appreciative.
The list of new capabilities for Kubernetes is simply astounding. Here are just a few:
Authentication RBAC HorizontalPodAutoscalers Batch Jobs CertificateSigningRequests ConfigMaps PersistentVolumes Daemonsets Deployments/DeploymentRollBack Ingress NetworkPolicy ThirdPartyResources StorageClasses Endpoints Secrets
Imagine being able to configure network policies through an automated StackStorm workflow based on a particular projects needs.
Think about how RBAC could be managed using our Kubernetes Authz Webhook through StackStorm.
Or how about kicking of Kubernetes Jobs to Administer some cluster level cleanup activity but handing that off to your NOC.
Or allowing your Operations team to patch a HorizontalPodAutoscaler through a UI.
We could build a metadata framework derived from the Kubernetes API annotations/labels for governance.
The possibilities are now literally endless. Mad props go out to Andy Moore for all his work in this endeavor.
Ok so why am I listing this as beta?
There is a freak ton of capabilities in our new st2 pack that we haven’t finished testing. So if you are adventurous, want to play with something new and can help us, we would love your feedback.
Thus far our testing has included the following:
Secrets Services Deployments Ingresses Physical Volumes Replication Controllers Quotas Service Accounts Namespaces Volumes
Hope you get as excited about this as we are. We now have a way to rapidly integrate Kubernetes with ….. well …… everything else.
@devoperandi
Note: As soon as we have cleaned up a few things with the generator for this pack, we’ll open source it to the community.
Past Blogs around this topic: